We use Tailscale which is amazing and have started using NextDNS for DNS lookups. I wanted to get the logs into our Sentinel SIEM solution and, after a lot of experimentation with various solutions, have settled on an Azure Logic App. As the process was not without its trials, I thought it would be useful to share the final configuration here.
You will need to have set up NextDNS on your devices(s) and Microsoft Sentinel in Azure. I use Tailscale to deploy NextDNS to all the devices.
To create a logic app go to the azure portal search for Logic Apps:
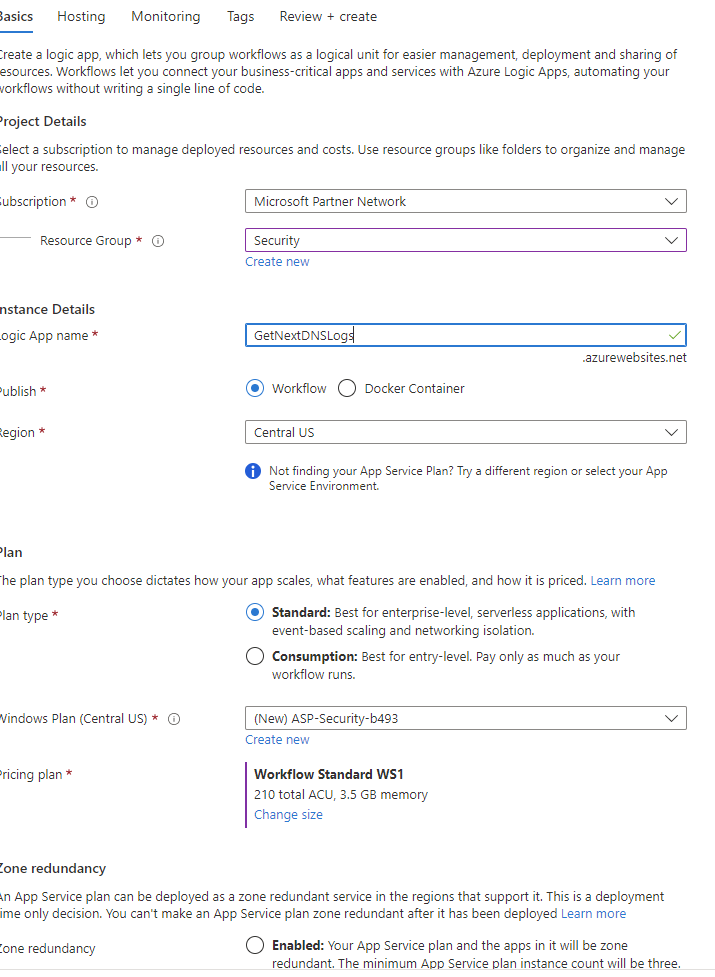
Click Add and select Workflow and Consumption Based
Once in the Logic App set it up to run every hour or day depending on how often you want to get the logs. Click New Step, search recurrence. Click Schedule.
I have set the Interval 1 witht the Frequency as Hour.
Click the plus to create the next step and serach for get past time:
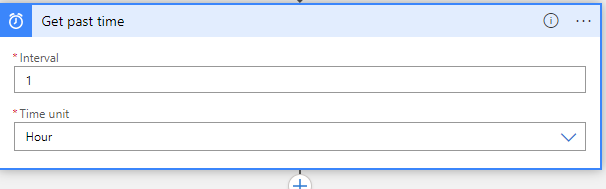
Here we want to create a new variable of a past time of 1 hour (or 1 day if we are collecting the logs every day).
Next step is a HTTP Request, you will need the profile ID for the API endpoint and your API Key from your account page:
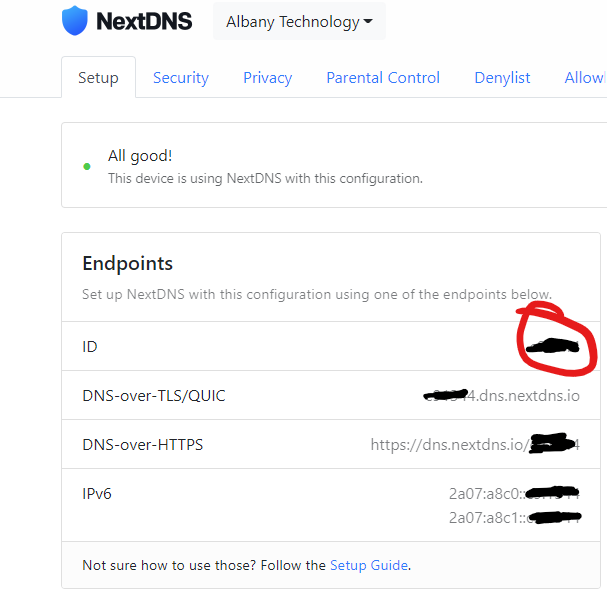
Click next step and search for HTTP request.
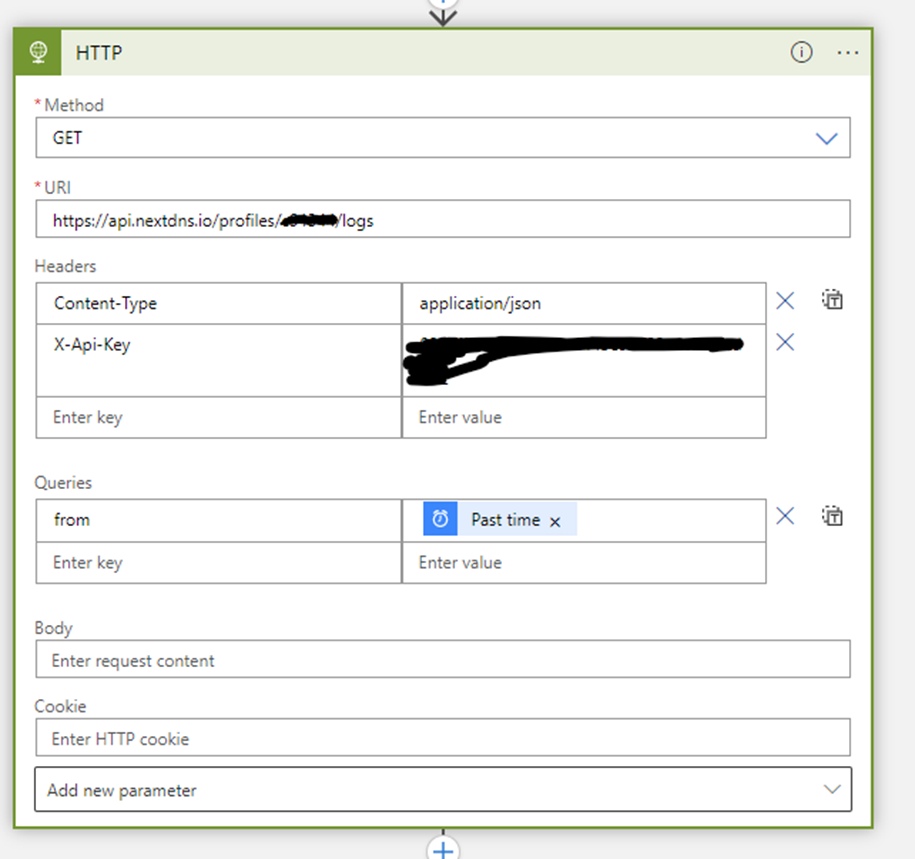
In the query section insert the Past Ime Variable so we get the logs for the last hour/day.
Next Parse the JSON:
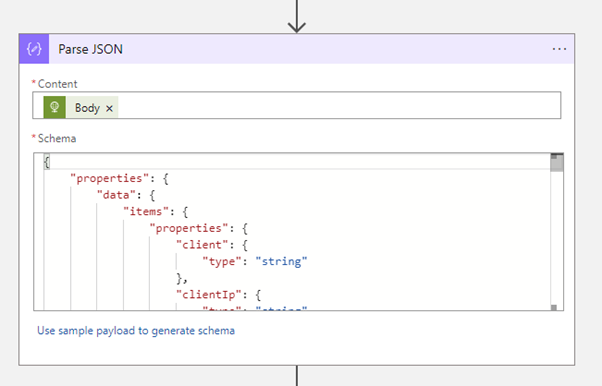
And use the following sample payload to generate the schema:
{
"data": [
{
"timestamp": "2021-03-18T03:00:10.338Z",
"domain": "21-courier.push.apple.com",
"root": "apple.com",
"tracker": "apple",
"encrypted": true,
"protocol": "DNS-over-HTTPS",
"clientIp": "2a01:e0a:2cd:87a0:1b23:2832:57cd:aa1d",
"client": "apple-profile",
"device": {
"id": "8TD1G",
"name": "Romain’s iPhone",
"model": "iPhone 12 Pro Max"
},
"status": "default",
"reasons": []
},
{
"timestamp": "2021-03-18T02:56:14.182Z",
"domain": "sb.scorecardresearch.com",
"root": "scorecardresearch.com",
"tracker": "scorecard_research_beacon",
"encrypted": false,
"protocol": "UDP",
"clientIp": "91.172.51.28",
"status": "blocked",
"reasons": [
{
"id": "blocklist:nextdns-recommended",
"name": "NextDNS Ads & Trackers Blocklist"
},
{
"id": "blocklist:oisd",
"name": "oisd"
}
]
}
]
}
Lastly send the parsed data to a Log Analytics Connector:
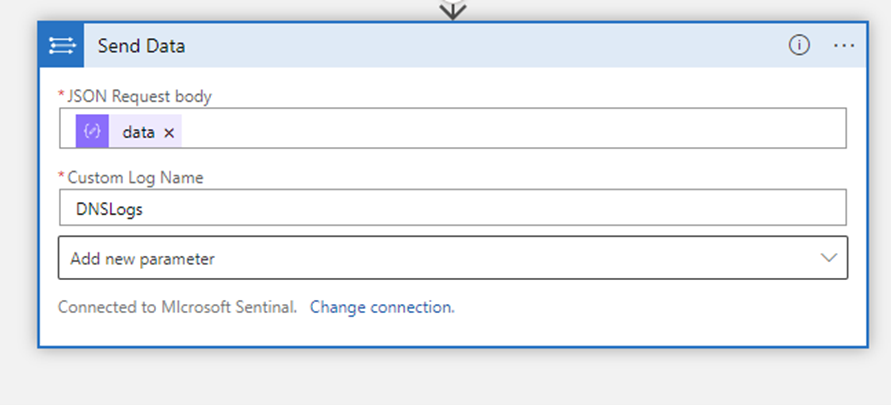
Get the Workspace ID and Key from Sentinel Workspace Settings Page.
Press Trigger and Run and the logic app should get the last hours logs and ship them to Sentinel. It takes about five minutes for them to appear in you log analytics workspace as a Custom Log.
Then you can run the following Query to see blocks that have occurred due to a security reason:
DNSLogs_CL
| where status_s contains "blocked"
| where reasons_s !contains "NextDNS Ads & Trackers Blocklist"
References
NextDNS API Documentation | api
Perform operations on data - Azure Logic Apps | Microsoft Learn







